Asset discovery
This involves identifying all assets within an organization, including hardware and software.
Seeward unifies existing tools in your security stack, creating a centralized hub to control the chaos of vulnerability analysis, triage, and remediation.
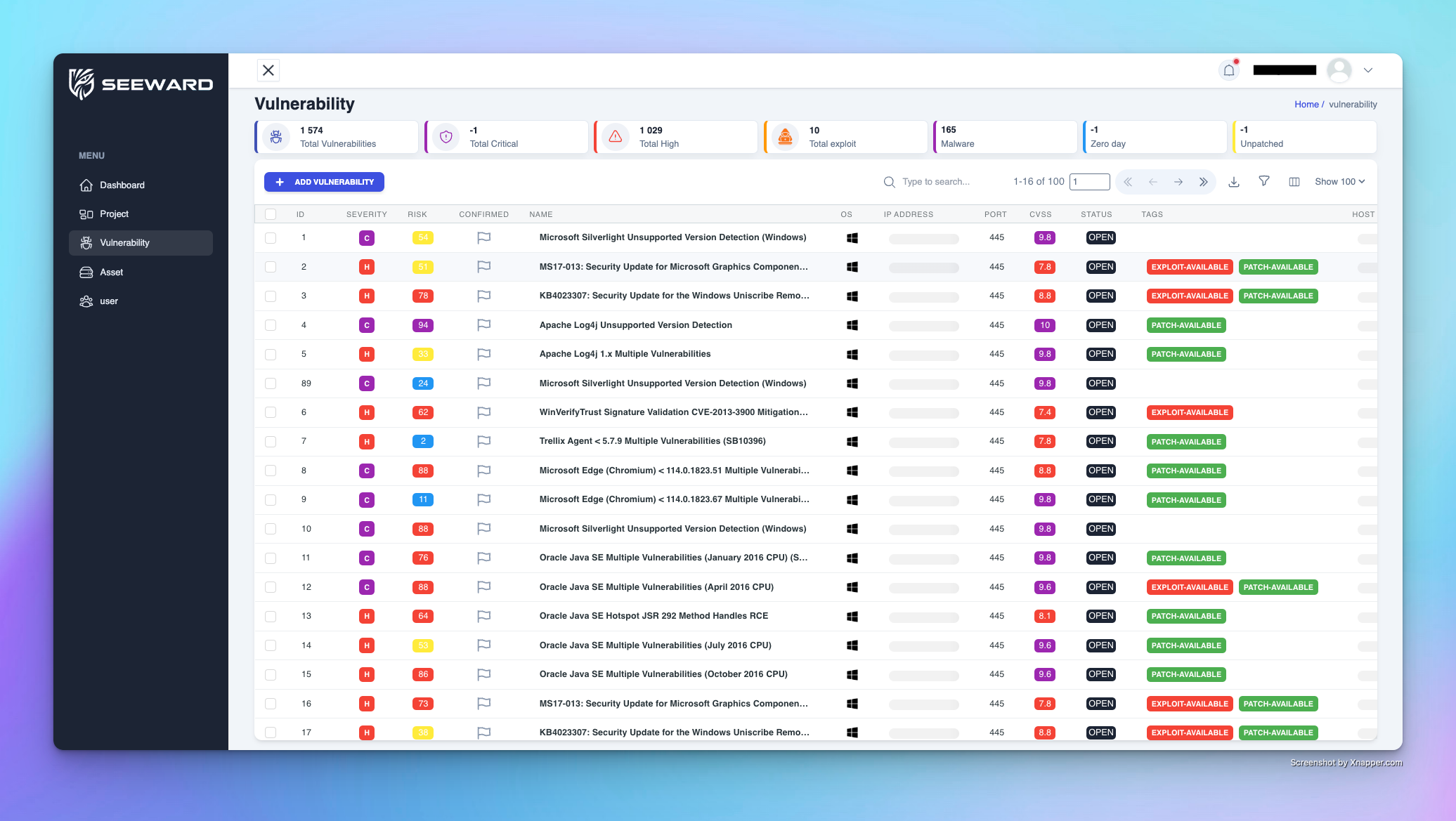

This involves identifying all assets within an organization, including hardware and software.
This involves scanning all assets for vulnerabilities
This involves analyzing the results of the vulnerability scan and asset discovery and assessing the level of risk associated with each vulnerability and asset.
This involves prioritizing vulnerabilities based on their level of risk.
This involves addressing vulnerabilities in order of priority, beginning with the most critical.